BLOG

Web application and API protection (WAAP) security: A guide to overcoming today’s complex digital landscape

Executive summary
Today, web applications are indispensable for businesses across all sectors. C8 Secure recognizes that the hybrid and multi-cloud environments, modern application architectures and the necessity of securing remote work whilst maintaining high service availability pose significant challenges in securing these applications. Our comprehensive approach to application security is designed to mitigate the many challenges of protecting web applications and APIs from a diverse range of threats.
Despite the availability of numerous web application security solutions, businesses often struggle due to resource constraints (budgetary and expertise), the complexity of modern applications (including microservices, API ecosystems and continuous updates), and issues with false positives and negatives resulting from outdated security policies.
In this blog, I’ll explore the current threat landscape for web applications, examine the biggest challenges in securing modern applications, highlight the business implications of security breaches and offer insights and best practices into navigating today’s ever-evolving digital landscape.
Evolving threat landscape and its implications
The threat landscape for web applications is ever-changing, presenting businesses with intricate challenges. Key aspects include:
- Human threats: These encompass hackers, insiders and other malicious actors who exploit vulnerabilities in web applications.
- Bot threats: Malicious bots are increasingly sophisticated, often used to breach user accounts with stolen credentials and mimic legitimate user behaviour, causing significant harm.
- OWASP Top 10 risks: Common attack vectors like (Structured Query Language) SQL injection and cross-site scripting highlight the critical security risks identified in the Open Web Application Security Project (OWASP) Top 10, necessitating robust security measures.
What are the biggest challenges in securing modern applications?
Modern applications are inherently difficult to secure due to several factors:
- Distributed infrastructure: Applications spread across data centres and cloud environments complicate security efforts.
- Microservices and APIs: These add complexity to data flows, making it harder to monitor and protect.
- Continuous Integration/Continuous Deployment (CI/CD): Frequent changes by development teams can introduce new vulnerabilities.
- Skilled resource shortage: The industry-wide lack of skilled security experts exacerbates these challenges.
- Evolving threats: Sophisticated and evolving threats require constant vigilance and advanced security solutions.
How security breaches impact your business
Failure to secure web applications and APIs can have far-reaching business consequences:
- Financial impact: Breaches can lead to substantial financial losses from both direct costs (response and recovery) and indirect costs (lost revenue and brand damage).
- Reputational damage: Customer trust and brand reputation can be severely affected, leading to customer churn and long-term damage.
- Regulatory and legal consequences: Non-compliance with data protection laws can result in hefty fines and legal penalties.
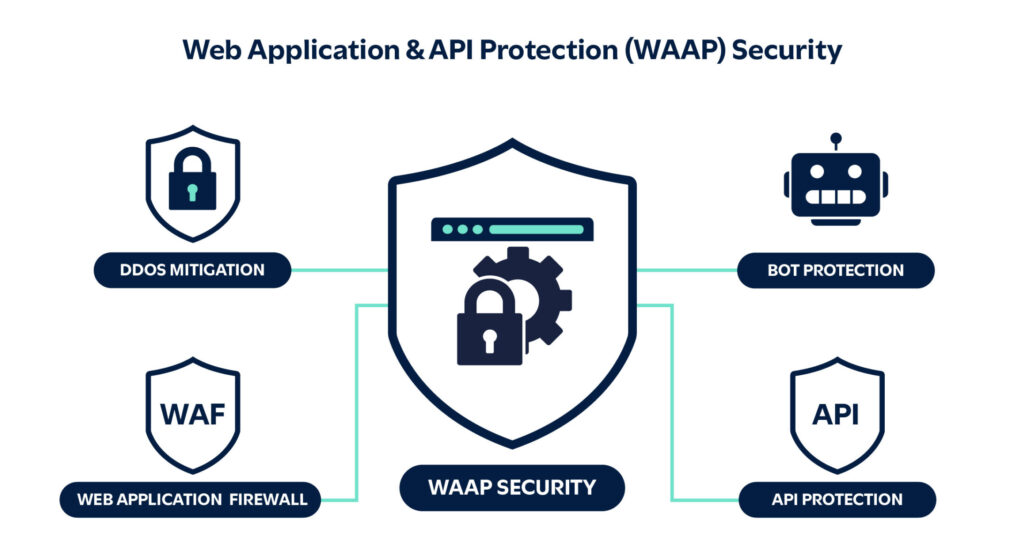
C8 Secure’s holistic application protection approach
To address these challenges, C8 Secure advocates for a comprehensive set of best practices in web application and API security:
- Regular Vulnerability Assessments and Penetration Testing (VAPT) assessments: Both automated and manual testing help identify and address weaknesses.
- Patch management: Keeping software and libraries up-to-date is crucial for preventing exploitations of known vulnerabilities.
- Secure coding practices: Training for development and operations teams on secure coding reduces the introduction of vulnerabilities.
- Web Application and API Protection (WAAP) security: Emphasis on authentication, authorization and rate limiting for APIs is essential.
- Incident response plan: A well-defined plan ensures quick and effective responses to security breaches.
Building a resilient web application and API security framework
Securing web applications is a complex challenge requiring a holistic approach. By understanding the evolving threat landscape, recognising the business implications of security breaches and implementing best practices, businesses can significantly enhance their security posture. C8 Secure is dedicated to providing robust security solutions that help businesses protect their critical web applications and APIs, ensuring resilience against the complex threats of today’s digital landscape.
C8 Secure WAAP solutions represent a proactive approach to web application and API security.
To support organizations enhance their web application and API security framework, C8 Secure is offering 3 months of FREE WAAP services for the first 50 customers to sign up to a 15-month contract*.
Learn more about the WAAP solution here.
For further information and detailed guidance on securing your web applications, email info@c8secure.com or fill out our Contact Us page.
*T&Cs apply. Limited-time offer; subject to change. First 3 months free, when signing up to a 15-month contract.
DOWNLOAD BROCHURE
For more information, please download our solutions brochure
Related content: C8 Secure in the Philippines
TESTIMONIAL
Philippine National Bank – Customer Spotlight
Hear from Roland Oscuro, FSVP, CISO, Philippine National Bank, who discusses his company’s partnership with C8 Secure, providing SOC services to the company.
C8 Secure - Philippine National Bank - Customer Spotlight
EVENT
C8 Secure CIO Philippines Summit 2024
Our C8 Secure team hosted a Cybersecurity Summit gathering the brightest minds, industry leaders, and executives from top organizations.
C8 Secure CIO Philippines Summit 2024