BLOG

DDoS explained: From threats to solutions – Insights into safeguarding your network
A Distributed Denial-of-Service (DDoS) attack, whether large or small, can cause significant downtime and financial loss.
 But what is exactly a DDoS attack?
But what is exactly a DDoS attack?
In this blog, Craig Lusher, Product Principal at C8 Secure, will explore what a DDoS attack is, the different types of DDoS attacks and the best practices for mitigating DDoS attacks.
What is a DDoS attack?
A DDoS attack is like an unexpected traffic jam on an otherwise free-flowing highway. The attacks attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming it with a flood of Internet traffic.
DDoS attacks leverage multiple compromised computer systems as sources of attack traffic, including computers and Internet of Things (IoT) devices. They involve networks of Internet-connected devices infected with malware, controlled remotely by attackers and forming a botnet.
The process begins with the attacker creating the botnet by infecting multiple devices. Next, they send remote commands to the botnet, which then sends numerous requests to the target’s IP address. This flood of requests overwhelms the server or network, resulting in a denial-of-service for legitimate traffic.
Several high-profile DDoS attacks have made headlines in recent months, showcasing the damage these attacks can inflict, regardless of industry.
- On August 9 and 10, DDoS attacks hit Final Fantasy 14 (FFXIV) online role-playing gaming data centers for two straight days. The DDoS attacks caused log-in delays and large-scale disconnections, preventing players from logging into the critically acclaimed massively multiplayer online role-playing game (MMORPG).
- On August 8, a DDoS attack targeted the Kursk Region’s local services, as per the Ministry of Digital Development, Communications and Mass Media of the Russian Federation. The perpetrators aimed to potentially disrupt social services, damage the online infrastructure and/or obtain access to user data, but all attacks were successfully thwarted.
- On July 30, a DDoS attack resulted in an eight-hour Azure outage. The Azure outage had global reach, impacting a subset of customers attempting to connect to a range of Azure, Microsoft 365 and Microsoft Purview services.
Types of DDoS attacks
DDoS attacks come in various forms. DDoS attacks can be categorized into three main types based on which part of the network connection they target.
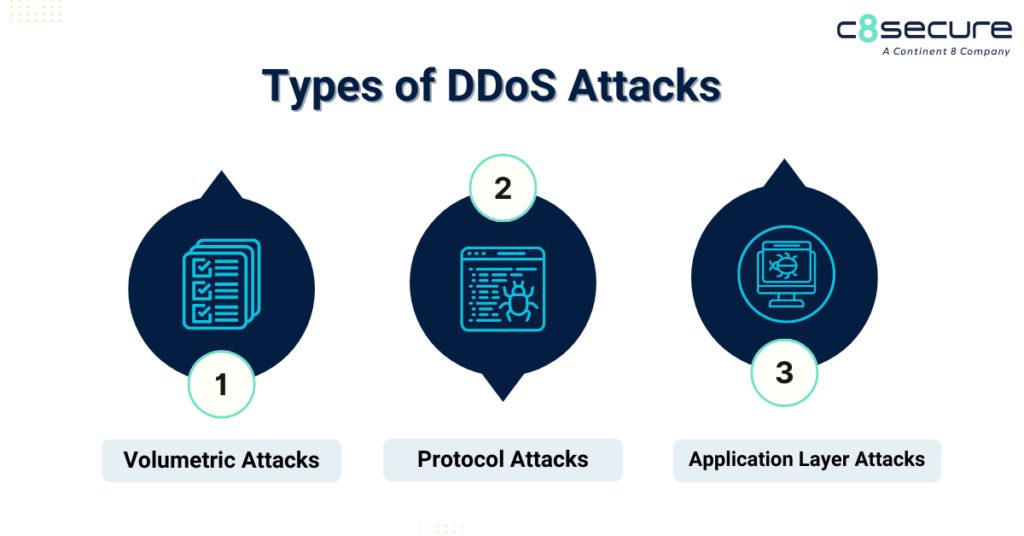
Volumetric attacks
A volumetric attack aims to overwhelm the bandwidth between the target and the Internet with massive amounts of data. The attack often uses amplification techniques to ensure it consumes all available bandwidth.
A good example is Domain Name System (DNS) amplification. This method is done through a small query to an open DNS server with a spoofed IP address, resulting in a large response being sent to the victim, ultimately overwhelming their bandwidth.
Protocol attacks
A protocol attack exploits weaknesses in network protocols, particularly layers 3 and 4 of the protocol stack. It disrupts service by consuming server resources or network equipment resources like firewalls and load balancers.
SYN flood is a popular method. It overwhelms the target by sending many TCP SYN packets with spoofed IP addresses, exhausting resources by never completing the TCP handshake.
Application layer attacks
The application layer attack targets the application itself, often appearing as legitimate traffic. It exhausts the target’s resources and creates a denial-of-service. The attack preys on the application layer (Layer 7 of the OSI model) where web pages are generated and delivered in response to HTTP requests.
HTTP flood method, for example, generates multiple HTTP requests to flood the server. These requests overwhelm the server and cause a denial-of-service. These can range from simple attacks with one URL and similar IP addresses to complex attacks using many IP addresses and random URLs.
Mitigation methods – A defense-in-depth, multi-layered approach
The main challenge in mitigating a DDoS attack is distinguishing between legitimate traffic and attack traffic. For example, a legitimate surge from a product release differs from an attack surge from known attackers.
These attacks are also multi-vector. This means they use multiple pathways to overwhelm targets, making it harder to distinguish between attack and normal traffic. A layered approach, such as combining DNS amplification (targeting layers 3/4) with an HTTP flood (layer 7), requires varied strategies for mitigation.
Due to these complexities, protecting a site from DDoS attacks requires a multi-layered approach. In the event of unforeseen circumstances, having a clear plan in place for responding to DDoS attacks can minimize downtime and damage.
Finding a service specializing in DDoS solutions can be a great help, but there are layers to the mitigation process.
- It begins with securing all devices and keeping them updated to prevent their compromise and inclusion in a botnet. Regular updates and patches are particularly crucial for mitigating application layer attacks.
- In DDoS mitigation, more redundancy means more reliability. Scaling network redundancy enhances reliability by distributing resources across multiple data centers, which helps balance the load during an attack. Increasing network bandwidth can also aid in handling volumetric attacks.
- Having on-demand capacity to increase the resources to the affected asset. This can be achieved by either expanding vertically, by adding larger throughput connectivity or laterally by adding additional connectivity or by using Content Delivery Networks (CDNs) which absorb excess traffic by taking the load off the origin servers.
- Implementing rate or connection limiting using Web Application Firewalls (WAFs). Rate and connection limiting controls the number of requests and connections a server accepts in a given timeframe.
- Effective traffic monitoring combined with behavioral analytics is essential for identifying and responding to unusual patterns. In this case, traffic analysis tools improve efficiency.
- Deploying WAFs and using advanced Intrusion Protection Systems (IPS) to act as a reverse proxy can help filter out malicious traffic. WAFs are also key to mitigating protocol attacks.
At C8 Secure, we advocate for a ‘defense-in-depth’ strategy, where multiple layers of security controls are implemented throughout the organization’s IT environment. This ensures that if one layer is breached, additional layers are in place to prevent or mitigate the attack.
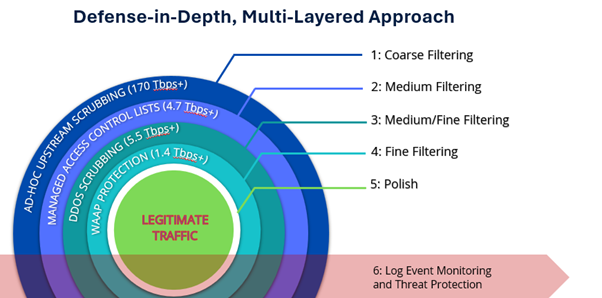
C8 Secure’s defense-in-depth, multi-layered approach includes:
- Coarse filtering: Ad-Hoc upstream traffic filtering and DDoS scrubbing
- Medium filtering: Managed access control lists at the network edge
- Medium/fine filtering: Layer 3 and 4 DDoS scrubbing
- Fine filtering: Layer 7 Web Application and API Protection (WAAP) rate limiting and filtering
- Polish: Traffic delivery with Endpoint Detection and Response/Managed Detection and Response (EDR/MDR) solutions and managed updates and hardening
- Log event monitoring and threat protection: Security Operations Centre (MSOC) and Security Incident and Event Management (SIEM) threat detection and response
C8 Secure for complete DDoS protection
C8 Secure offers the most comprehensive cybersecurity solutions equipped to meet today’s emerging DDoS threats.
- DDoS solution: Our DDoS service offers a global network with 5 Tbps> of DDoS scrubbing and network capability. This ensures businesses are protected from volumetric layer 3/4 attacks. We use multiple layers of protection in our DDoS system from best-of-bread technology partners to our own intellectual property and processes.
- EDR and MDR solutions: Our EDR and MDR services ensure comprehensive protection for endpoints against advanced threats such as ransomware, malware and phishing attempts. These solutions monitor endpoint activity in real-time, detect anomalies and respond to threats promptly.
- Firewall solution: Our Firewall service includes customisable IDS/IPS capabilities. When combined with our SOC service, IDS/IPS events are enriched with specific threat intelligence and ingested into our SIEM platform. Our SOC analysts can then deliver powerful insights into a customer’s current threat state and perimeter activities, providing detection, prevention and responses to known and emerging threats.
- SOC and SIEM solutions: Our SOC and SIEM services deliver continuous 24x7x365 monitoring, advanced threat detection to identify anomalies and potential risks, integrated threat intelligence to stay ahead of evolving and high-impact threats and a cutting-edge SIEM architecture for high-performance analytics and efficient incident management.
- WAAP solution: Our WAAP service defends web applications and APIs from threats like OWASP Top 10 vulnerabilities such as SQL injection, cross-site scripting, as well as credential stuffing, site scraping, malicious bots and other vulnerabilities and exploits. This cloud-based solution is scalable and flexible, allowing businesses to adapt their security measures as needed.
Cybersecurity solutions for a safer tomorrow
C8 Secure provides comprehensive, multi-layered threat prevention, detection and response solutions to secure your organization’s digital assets in the face of evolving cyber threats. For more information on how C8 Secure can support your cybersecurity initiatives, email info@c8secure.com or fill out our Contact Us page.
DOWNLOAD BROCHURE
For more information, please download our solutions brochure