BLOG

How Vulnerability Assessment and Penetration Testing (VAPT) can protect your business from cyber threats
Organizations face daily threats to their IT infrastructure, making Vulnerability Assessment and Penetration Testing (VAPT) an essential practice for maintaining security and meeting compliance.
Cybersecurity threats pose significant risks to organizations worldwide, potentially leading to substantial financial losses and reputational damage. Consequently, investing in robust cybersecurity maintenance for IT infrastructure is crucial for business continuity.

Security professionals employ various strategies to safeguard IT infrastructure from threats. Among these, Vulnerability Assessment and Penetration Testing (VAPT) stands out as a predominant and essential practice for cybersecurity. In fact, certain sectors even require organizations to perform this testing regularly.
In this blog, Craig Lusher, Product Principal at C8 Secure, examines the concept of VAPT, showcases VAPT in practice, provides a comprehensive guide to VAPT in cybersecurity and offers insights on selecting the right service provider.
What is VAPT?
VAPT is a testing methodology that combines vulnerability assessment with penetration testing to deliver a thorough security evaluation. Understanding the distinction between Vulnerability Assessment and Penetration Testing is crucial, as each serves different purposes.
A vulnerability assessment involves examining the security weaknesses within an organization’s infrastructure. In contrast, penetration testing, or pentesting, is a more assertive approach where the tester seeks to understand how these vulnerabilities could impact the system.
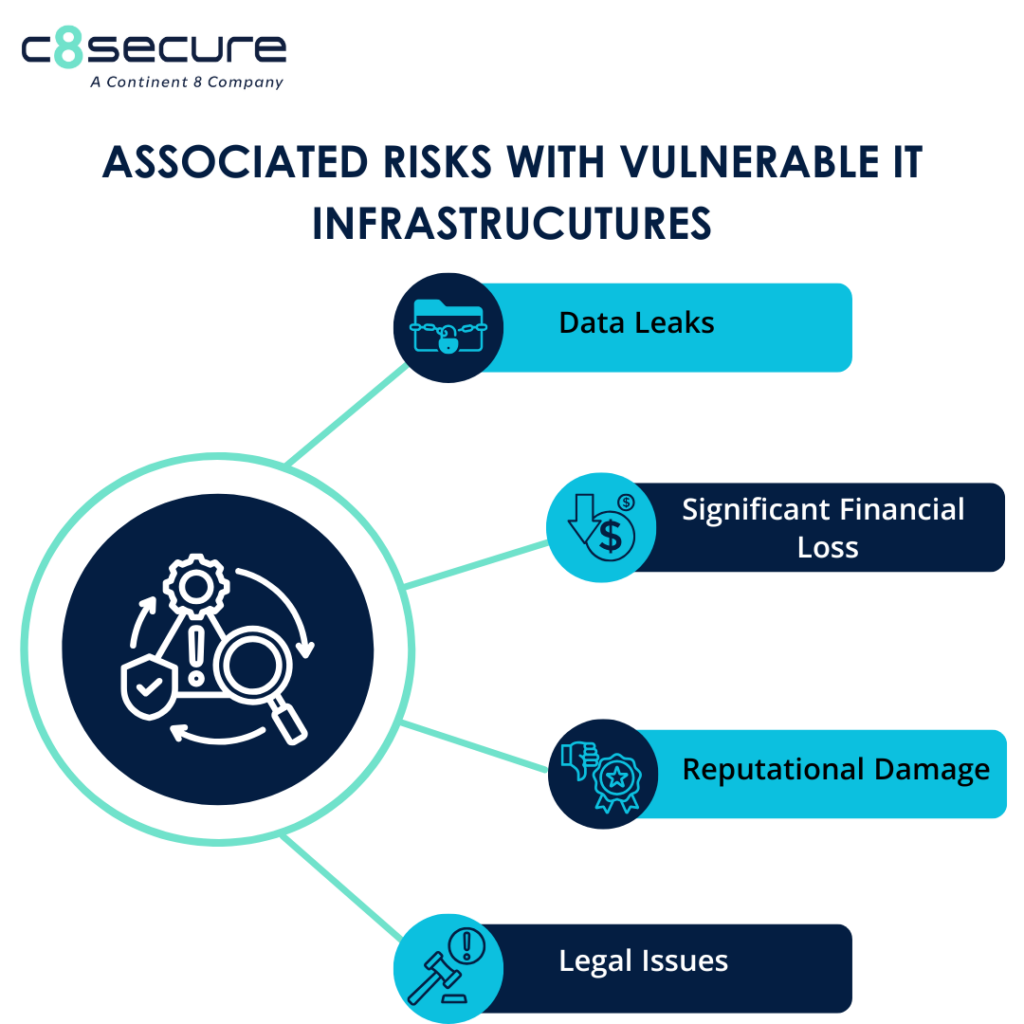
Recognizing the potential consequences of leaving these security vulnerabilities unmitigated highlights the importance of VAPT for the organization. Below are the risks that organizations may encounter with a vulnerable IT infrastructure.
-
Data leaks
Organizations safeguard critical assets such as financial information and customer data within their information systems. Authorized personnel access these assets regularly for routine day-to-day operations.
However, a compromised information system is susceptible to security breaches, potentially resulting in data leaks. A data leak occurs when an organization’s sensitive information is inadvertently exposed, either during transmission (e.g., online) or while stored (e.g., on laptops or hard drives). This information can then be exploited by unauthorized individuals for personal gain.
-
Significant financial losses
Security breaches can cause significant disruption to business operations. They may block employees’ network access, hindering their ability to perform daily duties and obstructing communication with external partners.
A company can incur substantial financial losses if it cannot function effectively, even for a single day. It risks missing production targets and losing business opportunities. Prolonged disruptions have forced some companies to lay off employees due to financial constraints.
-
Reputational damage
A company’s reputation is built on multiple factors, including its ability to ensure confidentiality. Data breaches can severely damage a company’s hard-earned reputation.
Customers and partners may sever ties due to diminished trust. Rebuilding public trust becomes increasingly challenging once reputational harm has been done. Therefore, implementing a robust security system to safeguard confidential data is crucial.
-
Legal issues
Regions generally enforce laws requiring companies to uphold data security. Non-compliance with these laws can result in penalties or suspension of data processing permissions.
Users can initiate legal action against a company for failing to protect their personal data. Legal proceedings are not only time-intensive but also costly, prompting many businesses to proactively implement data protection measures to avoid such dilemmas.
VAPT in practice
VAPT is mandatory for organizations across many sectors in the IT industry, including iGaming and online sports betting. The gaming sector is a great example where VAPT is required because of the sensitive nature of the business. A gaming organization stores the financial data of its customers. If a security breach occurs and the data falls into the wrong hands, the financial implications will be significant for the company and the customers.
Two recent, high-profile security breach examples involved MGM Resorts International and Caesars Entertainment:
- In September 2023, MGM Resorts suffered a 10-day cyber attack. The breach affected systems across Aria, Bellagio and MGM Grand, including corporate email, reservations, bookings and digital key card access. At the G2E 2023 gaming show, MGM CEO Bill Hornbuckle shared that the cyber attack disruption cost the company over $100 million.
- Caesars Entertainment fell victim to a cyber incident in the same month, and it appears that the same hacker group was behind the attack. “Scattered Spider” or “Roasted 0ktapus,” an affiliate of the Blackcat ransomware group that deploys their ALPHV malware during attacks, accessed the “Caesar’s Rewards” loyalty program database. Caesars reveals making a $15 million ransom payment to prevent sensitive information from being made public.
A thorough VAPT can prevent such an incident from happening. It can identify the internal and external vulnerabilities in the system to prevent unauthorized data access by irresponsible parties.
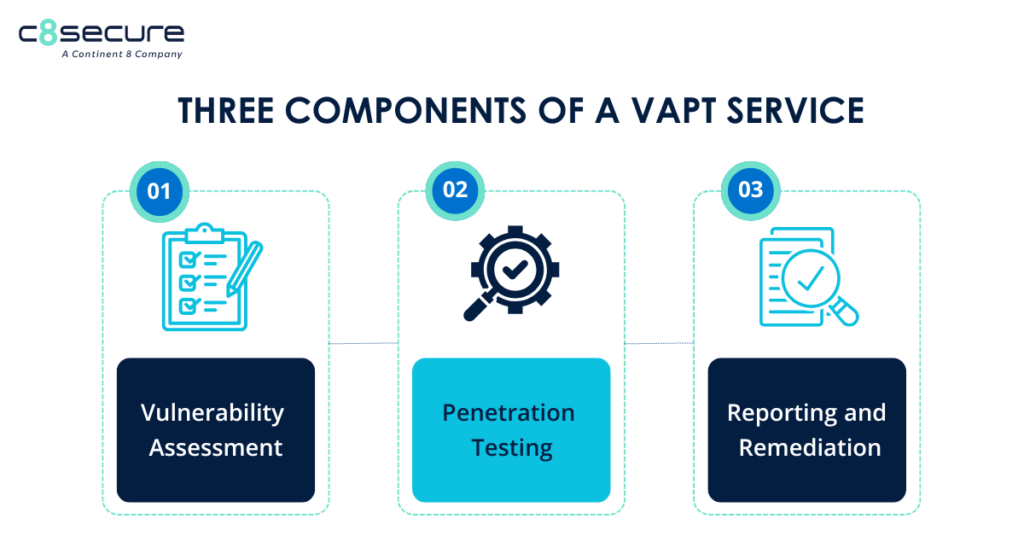
A closer look: The three-part process to VAPT
A comprehensive VAPT security assessment contains three major portions: Vulnerability Assessment (VA), Penetration Testing (PT) and reporting and remediation.
-
What is Vulnerability Assessment (VA)?
VA is a systematic process of identifying and quantifying vulnerabilities in an organization’s IT assets:
- VA involves scanning networks, systems and applications using automated tools and manual techniques to detect security weaknesses.
- VA helps organizations prioritize vulnerabilities based on their severity and potential impact on the business.
- Common vulnerabilities include misconfigurations, unpatched software, weak passwords and insecure protocols.
-
What is Pentesting (PT)?
Once vulnerabilities are identified, the security team advances to Pentesting (PT). PT, also known as ethical hacking, is a simulated attack on an organization’s IT infrastructure to evaluate its security posture:
- Skilled security professionals (penetration testers or pentesters) use a combination of tools and techniques to exploit identified vulnerabilities and gain unauthorized access to systems and data.
- PT helps organizations understand the real-world effectiveness of their security controls and incident response procedures.
- Types of PT include network pentesting, web application testing, mobile application testing and social engineering.
-
Reporting and remediation
After conducting VA and PT, a detailed report is prepared, highlighting the identified vulnerabilities, their severity and the potential impact on the organization:
- The report includes recommendations for remediation, such as patching software, strengthening access controls and improving security configurations.
- Organizations can use the report to prioritize and implement security improvements to reduce their risk exposure.
Choosing the right VAPT service provider
Given the critical role of VAPT for any organization, selecting the right service provider is crucial. While cost is an important factor to many, there are several other considerations when choosing a VAPT service for your enterprise.
Engage with seasoned professionals to ensure you maximize value. Experienced VAPT specialists can efficiently identify system vulnerabilities and devise solutions.
Furthermore, the provider must possess a comprehensive understanding of industry regulations. As these standards are frequently updated by regulatory bodies, the provider must stay informed of the latest developments.
C8 Secure – A trusted VAPT service provider
C8 Secure, a managed security service provider (MSSP), offers VAPT services to industries such as finance, healthcare and iGaming and online sports betting. These services offer comprehensive security assessments of IT infrastructures and applications, assisting companies in meeting regulatory requirements, identifying vulnerabilities and enhancing their cybersecurity framework.
The C8 Secure team is dedicated to conducting an all-encompassing VAPT service to evaluate the security posture of the customer’s external and internal IT assets. Their certified security professionals collaborate closely with the customer’s team to establish the scope and objectives of the assessment. The VAPT encompasses rigorous testing of security aspects, including information gathering, configuration testing, authentication testing, session management testing and data validation, in adherence to the OWASP Top 10 standards.
This assessment employs a combination of automated tools and manual techniques to meticulously identify potential vulnerabilities and weaknesses in the customer’s systems. Upon completion, the customer receives a detailed report that outlines the findings, risk ratings and recommended remediation actions.
By engaging in regularly scheduled VAPT services, customers can ensure the compliance and robustness of their systems and safeguard sensitive end-user data. This proactive approach also helps customers stay ahead of the evolving cyber threat landscape, continuously enhancing their security posture while maintaining customer trust, managing reputation and supporting financial growth and stability.
Cybersecurity solutions for a safer tomorrow
C8 Secure provides comprehensive, multi-layered threat prevention, detection and response solutions to secure your organization’s digital assets in the face of evolving cyber threats. For more information on how C8 Secure can support your cybersecurity initiatives, email info@c8secure.com or fill out our Contact Us page.
DOWNLOAD BROCHURE
For more information, please download our solutions brochure