BLOG

Zero Trust: Exploring the “never trust, always verify” cybersecurity framework
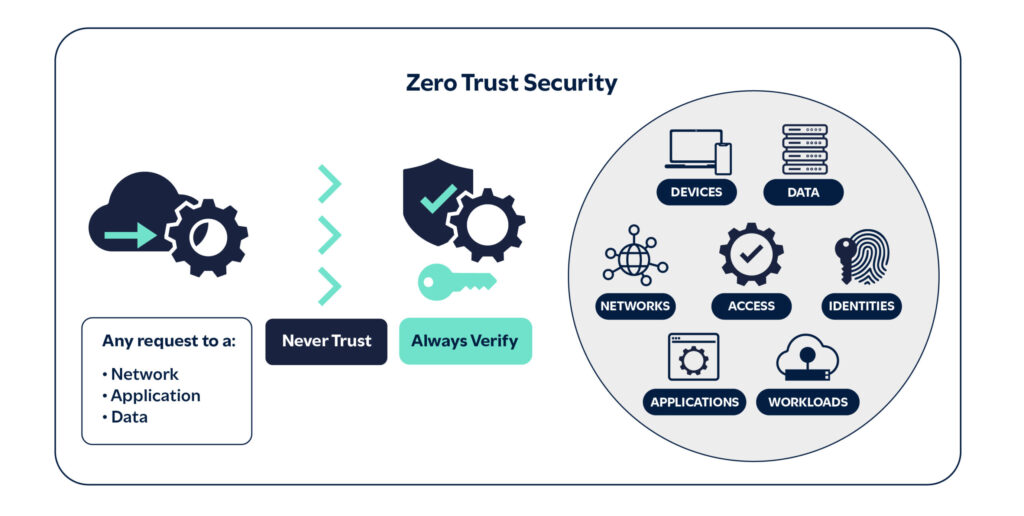
Zero Trust is a cybersecurity approach that emphasizes ongoing authentication, authorization and validation of all users, irrespective of their location relative to the organization’s network. This framework disregards traditional network boundaries, operating under the assumption that threats can exist both inside and outside the network.
While Zero Trust is not uniformly defined across the industry, various standards from established organizations offer guidelines for its implementation.
In this blog, we will explore how Zero Trust works, highlight the core tenants of the approach and examine the use cases and benefits of the cybersecurity platform.
How Zero Trust works
The core principle of Zero Trust is ‘never trust, always verify.’ This is achieved through rigorous user authentication and restricting access to the bare minimum required. The framework utilizes multi-factor authentication (MFA) based on risk assessment, identity protection measures, cutting-edge endpoint security and secure cloud technology.
These tools work together to continuously evaluate a user’s or system’s legitimacy, their access needs at any given moment and the overall system security. Data encryption, email security and ensuring the security of assets and endpoints before connection are also integral to the cybersecurity framework.
Zero Trust vs ‘trust but verify’ model
The Zero Trust approach represents a significant shift from the outdated ‘trust but verify’ network security model, which assumed inherent trust for users and endpoints within a network perimeter. This conventional model became less effective with the shift to cloud-based operations and the emergence of distributed work environments, particularly post-2020.
Under Zero Trust, organizations perpetually monitor and confirm that users and their devices are appropriately authorized and comply with the necessary policies. This process involves understanding and managing all service and privileged accounts, as well as determining their connectivity limits. Continuous validation is essential in Zero Trust, as threats and user attributes can change over time.
Enforcing Zero Trust policies requires real-time insight into various user and application identity attributes. This includes monitoring user identities, device privileges, behavior patterns, geographic locations, firmware versions, operating systems, installed applications and security incident detections. Leveraging analytics, incorporating vast amounts of enterprise data and utilizing artificial intelligence (AI) and machine learning (ML) models for policy decisions are crucial for effective implementation.
Since a significant percentage of cyber attacks involve credential misuse, Zero Trust also extends to credential and data protection strategies. This includes enhanced email security and secure web gateways, which helps maintain password integrity, account security and compliance with organizational policies, while preventing the use of risky shadow IT services.
Tenants of Zero Trust include:
- All data sources and computing services are considered resources.
-
- A network can consist of multiple classes of devices.
- A network might include small footprint devices that send data to aggregators/storage, use software as a service (SaaS), transmit instructions to actuators and perform other functions.
- An enterprise might decide to classify personally owned devices as resources if they can access enterprise-owned resources.
- All communications are secured regardless of network location.
-
- Network location alone does not imply trust.
- Access requests from assets located on enterprise-owned network infrastructure (e.g., inside a legacy network perimeter) must meet the same security requirements as access requests and communication from any other non-enterprise-owned network. In other words, trust should not be automatically granted based on a device’s presence within the enterprise network infrastructure.
- All communications should be conducted in the most secure manner possible, protecting confidentiality and integrity and providing source authentication.
- Access to individual enterprise resources is granted on a per-session basis.
-
- Trust in the requester is evaluated before access is approved.
- Access should be granted with the least privileges needed to complete the task. This might mean only ‘recently’ for a particular transaction and may not occur directly before initiating a session or performing a transaction with a resource. However, authentication and authorization to one resource will not automatically grant access to a different resource.
- Access to resources is determined by dynamic policy – including the observable state of client identity, application/service and the requesting asset – and may include other behavioral and environmental attributes.
-
- An organization protects resources by defining what resources it has, who its members are (or the ability to authenticate users from a federated community) and what access to resources those members need.
- For zero trust, client identity can include the user account (or service identity) and any associated attributes assigned by the enterprise to that account or artifacts to authenticate automated tasks.
- The state of the requesting asset can include device characteristics such as installed software versions, network location, time/date of request, previously observed behavior and installed credentials.
- Behavioral attributes include, but are not limited to, automated subject analytics, device analytics and measured deviations from observed usage patterns.
- Policy is the set of access rules based on attributes that an organization assigns to a subject, data asset or application.
- Environmental attributes may include such factors as requestor network location, time, reported active attacks, etc.
- These rules and attributes are based on the needs of the business process and acceptable level of risk.
- Resource access and action permission policies can vary based on the sensitivity of the resource/data.
- Least privilege principles are applied to restrict both visibility and accessibility.
- The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
-
- No asset is inherently trusted.
- The enterprise evaluates the security posture of the asset when evaluating a resource request.
- An enterprise implementing a Zero Trust Architecture (ZTA) should establish a continuous diagnostics and mitigation (CDM) system or equivalent to monitor the state of devices and applications, applying patches and fixes as needed.
- Assets that are discovered to be subverted, having known vulnerabilities or not managed by the enterprise may be treated differently – including denial of all connections to enterprise resources – than devices owned by or associated with the enterprise that are deemed to be in their most secure state. This may also apply to associated devices (e.g., personally owned devices) that may be allowed to access some resources but not others. This, too, requires a robust monitoring and reporting system in place to provide actionable data about the current state of enterprise resources.
- All resource authentication and authorization processes are dynamic and strictly enforced before access is allowed.
-
- This is a constant cycle of obtaining access, scanning and assessing threats, adaptation and ongoing trust reevaluation in communications.
- An enterprise implementing a ZTA would be expected to have Identity, Credential and Access Management (ICAM) and asset management systems in place. This includes the use of multi-factor authentication (MFA) for accessing some or all enterprise resources.
- Continuous monitoring, with possible reauthentication and reauthorization occurs throughout user transactions, as defined and enforced by policy (e.g., time-based, new resource requested, resource modification, anomalous subject activity detected), aiming to balance security, availability, usability and cost-efficiency.
- The enterprise collects as much information as possible about the current state of assets, network infrastructure and communications and uses it to improve its security posture.
-
- An enterprise should collect data about asset security posture, network traffic and access requests, process that data and use any insights gained to improve policy creation and enforcement. This data can also be used to provide context for access requests from subjects.
It is important to note that continuous monitoring is core to the Zero Trust tenants.
Zero Trust use cases
Zero Trust architecture is increasingly relevant for organizations that rely on network-based operations and handle digital data. Its application spans several common scenarios:
Firstly, many organizations are looking at Zero Trust to either replace or enhance their existing VPN solutions. While VPNs have traditionally been a cornerstone for secure data access, they may not adequately address the complexities and risks of current cybersecurity threats. Zero Trust offers a more robust solution by continuously verifying every access request, regardless of the location or nature of the network.
Another key application of Zero Trust is in supporting remote work. Unlike VPNs, which can create bottlenecks and reduce productivity due to their centralized nature, Zero Trust allows secure and efficient access control for remote connections. This approach aligns well with organizations deploying remote and distributed workforces, ensuring that security measures don’t compromise productivity.
Zero Trust plays a crucial role in cloud computing, particularly in multi-cloud environments. It ensures rigorous verification of all requests across cloud services, which helps mitigate the risks associated with unauthorized cloud services, often referred to as ’shadow IT.’ This approach empowers organizations to control and potentially block the use of unsanctioned applications, enhancing security in cloud-based operations.
For organizations that frequently onboard third parties and contractors, Zero Trust effectively extends secure, restricted access. This is particularly advantageous since these external parties often use devices not managed by the organization’s internal IT teams, posing a potential security risk.
Lastly, in rapidly growing organizations, Zero Trust facilitates the swift onboarding of new employees. It is a scalable solution that offers a stark contrast to conventional VPN setups, which might need additional capacity to accommodate a growing number of users. This makes Zero Trust an agile and adaptable solution for dynamic and expanding business environments.
Benefits of Zero Trust
Cloud computing environments are becoming prime targets for cybercriminals. These adversaries often aim at stealing, corrupting or holding hostage crucial business data, including personally identifiable information (PII), intellectual property (IP) and financial records.
In this context, Zero Trust is effective for:
- Minimizing the potential for attacks and decreasing the likelihood of data breaches.
- Offering detailed access control within cloud environments and for containerized applications.
- Diminishing both the impact and severity of successful attacks, which in turn reduces the time and expense involved in recovery.
- Assisting in meeting various compliance requirements.
The Zero Trust model is also crucial in IT infrastructures that are characterized by the extensive distribution of cloud resources, data and endpoints. This heightened level of scrutiny eases the burden for IT and security professionals, from administrators to Chief Information Security Officers (CISOs).
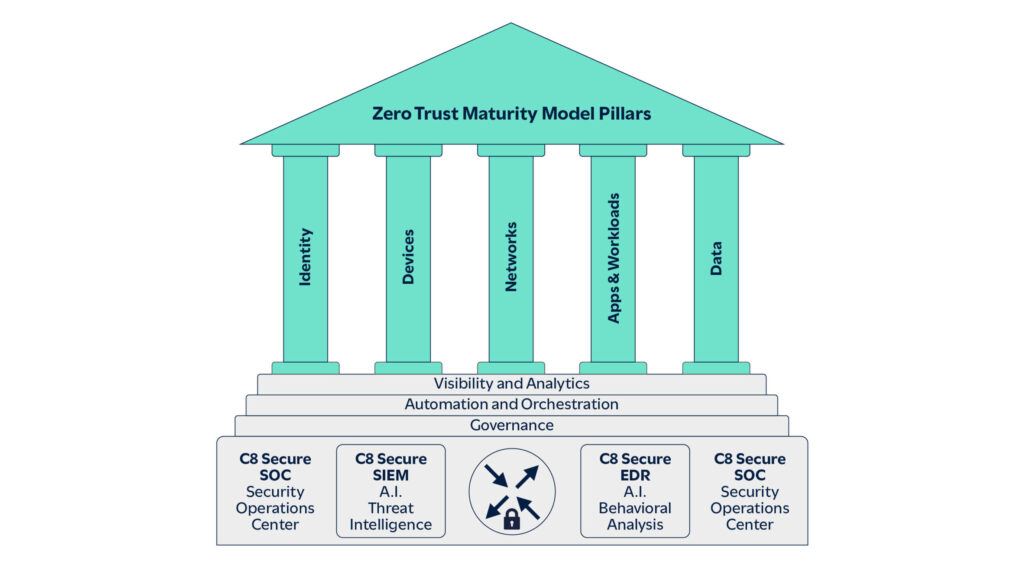
Zero Trust has numerous components to make up the Zero Trust Architecture (ZTA), including:
- Policy Engine (PE): Responsible for the ultimate decision to grant access to a resource for a given subject.
- Policy Administrator (PA): Establishes and/or shuts down the communication path between a subject and a resource (via commands to relevant Policy Enforcement Points or PEPs).
- Policy Enforcement Point (PEP): Enables, monitors and eventually terminates connections between a subject and an enterprise resource.
- Continuous Diagnostics and Mitigation (CDM) System: Gathers information about the enterprise asset’s current state and applies updates to configuration and software components.
- Industry Compliance System: Ensures that the enterprise remains compliant with any regulatory regime that it may fall under (e.g., Federal Information Security Management Act or FISMA, healthcare or financial industry information security requirements).
- Threat Intelligence Feeds: Provides information from internal or external sources that help the policy engine make access decisions.
- Network and System Activity Logs: Aggregates asset logs, network traffic, resource access actions and other events that provide real-time (or near-real-time) feedback on the security posture of enterprise information systems.
- Data Access Policies: Define the attributes, rules, and policies about access to enterprise resources.
- Enterprise Public Key Infrastructure (PKI): Generates and logs certificates issued by the enterprise to resources, subjects, services and applications.
- ID Management System: Creates, stores and manages enterprise user accounts and identity records (e.g., lightweight directory access protocol or LDAP server).
- Security Information and Event Management (SIEM) System: Collects security-centric information for later analysis. This data is then used to refine policies and warn of possible attacks against enterprise assets.
How C8 Secure’s Managed SOC and SIEM solutions helps
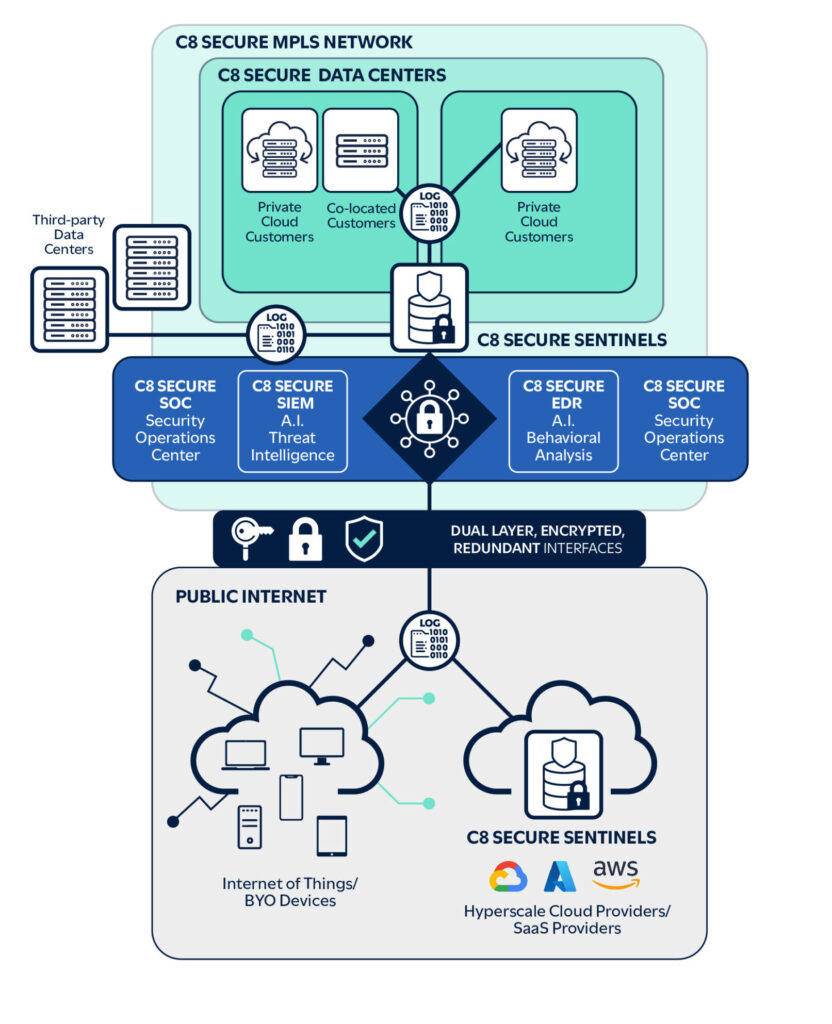
C8 Secure’s Managed Security Operations Center (SOC) and SIEM solution provides the SIEM platform, threat intelligence feeds, 24/7 analysts and a repository for network and system log events. By leveraging artificial intelligence (AI) and machine learning (ML) with detection rules, suspicious events are correlated and investigated. Customer data sources can include traditional data centers, on-prem, remote workers and various hyperscaler cloud and SaaS providers.
In addition, C8 Secure’s Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR) solution can provide an enhanced level of control at the device level for investigation and remediation. Remediation can be manual or leverage the integrated Security Orchestration, Automation and Response (SOAR) capabilities for quick, automated responses. The following architecture illustrates these components.
Implementing Zero Trust with C8 Secure
We understand that implementing Zero Trust is about enhancing, not replacing, your existing network infrastructure. Our proactive prevention, detection and response approach integrates seamlessly with critical components like identity and access management, leveraging and complementing your current security tools and practices. We adapt these elements to align with the Zero Trust model, ensuring a robust and resilient defense against evolving cyber threats.
Choosing us for your Zero Trust implementation means entrusting your network’s security to experts committed to strengthening your cybersecurity posture. Our comprehensive, multi-layered services provide complete, 360-degree protection while maintaining the integrity and efficiency of your current systems. Discover how we can transform your network’s security at C8 Secure.
Cybersecurity solutions for a safer tomorrow
C8 Secure provides comprehensive, multi-layered threat prevention, detection and response solutions to secure your organization’s digital assets in the face of evolving cyber threats. For more information on how C8 Secure can support your cybersecurity initiatives, email info@c8secure.com or fill out our Contact Us page.
DOWNLOAD BROCHURE
For more information, please download our solutions brochure
Related content: C8 Secure in the Philippines
TESTIMONIAL
Philippine National Bank – Customer Spotlight
Hear from Roland Oscuro, FSVP, CISO, Philippine National Bank, who discusses his company’s partnership with C8 Secure, providing SOC services to the company.
C8 Secure - Philippine National Bank - Customer Spotlight
EVENT
C8 Secure CIO Philippines Summit 2024
Our C8 Secure team hosted a Cybersecurity Summit gathering the brightest minds, industry leaders, and executives from top organizations.
C8 Secure CIO Philippines Summit 2024