In our next edition of our “In the Spotlight” profile series, we feature Ben Sutton, Apprentice Security Operations Center (SOC) Analyst, based in the United Kingdom.
 In this Q&A, Ben shares insights into his foundational passion for cybersecurity, the value of practical, dynamic learning in a continually evolving landscape and the joy he derives from addressing complex technical challenges.
In this Q&A, Ben shares insights into his foundational passion for cybersecurity, the value of practical, dynamic learning in a continually evolving landscape and the joy he derives from addressing complex technical challenges.
Hello Ben, could you please provide us with an overview of your background and your responsibilities as an Apprentice SOC Analyst at Continent 8 Technologies and C8 Secure?
Of course! I joined the company in 2023 when I was 17. I started with a six-month internship as a Cybersecurity Intern in the Security Operations (SecOps) team, working in the evenings after school. Here, I was introduced to the roles and responsibilities that my team dealt with daily, gaining fantastic insight and experience into what it takes to keep Continent 8 and C8 Secure secure.
After I finished my final exams in 2024, the team started to transition our responsibilities as the company continued to expand its Managed SOC (MSOC) solution for both Continent 8 and C8 Secure customers. While the team grew and matured, I secured a placement in a cybersecurity apprenticeship degree course, allowing me to earn a well-recognised degree alongside gaining practical experience and knowledge from working in the SOC team.
My immediate role is to monitor, analyse and respond to security incidents for both Continent 8, C8 Secure and our worldwide customers. However, I also get involved in the engineering side of the SOC – building bespoke solutions and tooling for customer requests, such as custom alert reporting or improvements on systems or processes.
What led you to pursue a career in the cybersecurity field?
When I was a young child finishing primary school (the UK equivalent of Grade 6 in the US), we were asked what we wanted to be when we grew up. While my classmates gave typical answers such as astronaut, firefighter or doctor, I responded with, “anti-hacker.” From an early age, I’ve been deeply passionate about cybersecurity and technology, it’s something that has always felt instinctive to me. My friends, family and peers have always known that a future in cybersecurity was my destiny.
Cybersecurity is a constantly evolving field, one that changes daily and rarely offers a permanent solution to any problem. This ever-shifting landscape demands continuous creativity, adaptability and ingenuity. It creates a unique environment where innovative thinking is essential. For me, that dynamic nature is what makes cybersecurity so compelling: it offers endless opportunities to think outside the box and tackle some of the most complex challenges in the digital world.
What inspired you to join the SOC team, and what aspects of your job do you find most fulfilling?
Cybersecurity has always been the field I’ve wanted to work in, and joining the SOC team gave me a rare opportunity to engage directly with real-world threats. I believe the best way to learn is through hands-on experience; analyzing systems, identifying threats and responding to incidents has helped me develop skills and knowledge far beyond what I could gain in a classroom. Being a SOC analyst has truly accelerated my growth, and building confidence in my abilities has been one of the most fulfilling aspects of the role.
In addition, being part of the SOC has exposed me to the engineering side – understanding how systems work at a deeper level and even how they’re built. This perspective has given me a more complete understanding of SOC operations. I especially enjoy the unique technical challenges that come with it; problems that push me to think creatively and develop smart, effective solutions. There’s nothing more satisfying than solving a tough problem with an elegant approach.
Can you describe some of the challenges you encounter in your role? How do you also ensure you remain informed about the latest developments in security and cybersecurity?
As our customer base grows and our coverage expands, we’re dealing with increasing volumes of alerts and data during investigations. One key challenge that I embrace is coordinating effectively within the on-shift SOC team to manage the workload. Ensuring that alerts are thoroughly investigated and resolved in a timely manner requires strong, fast-paced communication and organization to keep everything flowing smoothly.
Perhaps more of an opportunity than challenge is prevalent industry issue of alert fatigue – when a specific alert generates so many false positives that it becomes difficult to stay motivated. As a Managed Security Services Provider (MSSP), our dedicated team of cybersecurity experts gladly take on the ‘alert fatigue’ responsibility. Managing this is a shared responsibility between analysts and engineers, involving regular review and tuning of detections to reduce noise and improve accuracy.
Given how fast cybersecurity evolves, staying up to date is essential. I do this in two main ways: first, by following curated newsfeeds and sources such as tl;dr sec and BleepingComputer for quick updates; second, by diving into technical whitepapers and in-depth analyses of complex attacks to understand how breaches occurred and what made them possible. A few standout examples for me are To Kill a Centrifuge (Stuxnet) and Wolves in the Repository (XZ Utils supply chain attack). I also enjoy deep-dive videos from LowLevelTV on YouTube, which break down everything from internet outages to CPU microcode vulnerabilities at a low level.
Can you provide insights into some of the new initiatives you are currently working on?
I’m currently leading a project to enhance our phishing simulation campaigns. While we use enterprise-grade email protection that blocks most generic phishing attempts, more sophisticated attacks can still slip through. These often involve techniques like simulating conversations, using compromised legitimate domains (e.g., vendors or customers) or redirecting through trusted websites to build a false sense of security – especially with the rise of AI-driven attacks. Since staff are often the final line of defense, the goal is to train users to recognize and respond to more advanced, harder-to-spot phishing emails, not just the obvious ones.
I’m also working on a project to enrich the Microsoft Defender logs we collect from customers. Defender spans multiple security areas – Office 365, identity, email, endpoints and more – so enhancing this data allows us to build more insightful dashboards, improve alerting and accelerate investigations. This enrichment helps us detect threats more effectively and respond faster, ultimately providing greater value and visibility to our customers.
Any final thoughts?
I am very thankful for the opportunities and support provided by Continent 8, C8 Secure, my manager Gina Qu and our Chief Security Officer, Patrick Gardner. I am excited about the future and look forward to continued growth and success with the team.






 Hello Chand, you completed your one-year anniversary earlier this year. Can you tell us how your first year has gone?
Hello Chand, you completed your one-year anniversary earlier this year. Can you tell us how your first year has gone?










 In this Q&A, Ben shares insights into his foundational passion for cybersecurity, the value of practical, dynamic learning in a continually evolving landscape and the joy he derives from addressing complex technical challenges.
In this Q&A, Ben shares insights into his foundational passion for cybersecurity, the value of practical, dynamic learning in a continually evolving landscape and the joy he derives from addressing complex technical challenges.

 In today’s digital world, cyber threats lurk around every corner. From sneaky malware to sophisticated ransomware, attackers are relentless. So, how do you stay one step ahead? The answer lies in cybersecurity assessments, with Vulnerability Assessment and Penetration Testing (VAPT) leading the charge. At C8 Secure, we’re passionate about helping businesses like yours fortify their defenses. Let’s dive into why VAPT and risk assessments are game-changers for securing your organization.
In today’s digital world, cyber threats lurk around every corner. From sneaky malware to sophisticated ransomware, attackers are relentless. So, how do you stay one step ahead? The answer lies in cybersecurity assessments, with Vulnerability Assessment and Penetration Testing (VAPT) leading the charge. At C8 Secure, we’re passionate about helping businesses like yours fortify their defenses. Let’s dive into why VAPT and risk assessments are game-changers for securing your organization.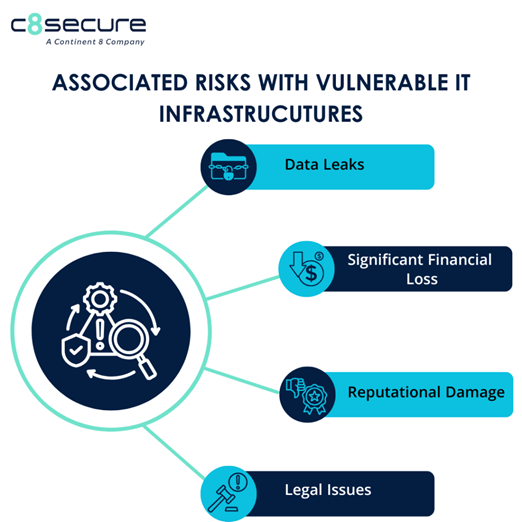


 In this Q&A, Gina expresses her enduring passion for cybersecurity, the challenges and opportunities she encounters with an expanding SOC team and platform and her unique insights on C8 Secure’s evolving SOC journey.
In this Q&A, Gina expresses her enduring passion for cybersecurity, the challenges and opportunities she encounters with an expanding SOC team and platform and her unique insights on C8 Secure’s evolving SOC journey.