DDoS PROTECTION
Safeguard your online services and maintain business operations with comprehensive perimeter network mitigation against DDoS attacks.
DISTRIBUTED DENIAL OF SERVICE (DDoS)
C8 Secure’s DDoS services deliver holistic L3-7 security that leverage our advanced, multi-layered cloud DDoS protection capabilities and cloud WAAP’s rate and connection limiting features. Our countermeasures encompass 50 Tbps of global internet connectivity and a worldwide network infrastructure.
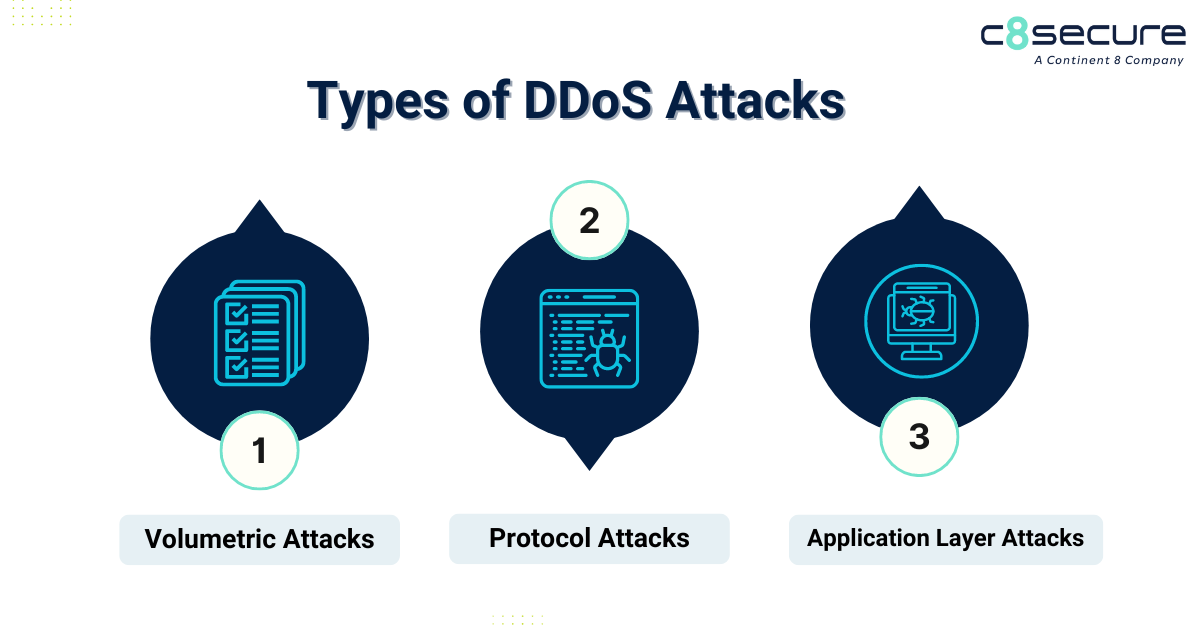
Types of DDoS attacks
DDoS attacks come in various forms. DDoS attacks can be categorized into three main types based on which part of the network connection they target.
Seamless DDoS Defense
Seamless DDoS Defense
Reduce mitigation time and maintain low latency levels, even under attack, with inline DDoS protection that automatically filters and cleanses internet traffic before it reaches your internet ports.
Flexible Options
Flexible Options
Benefit from a collaborative approach that caters to your exact on-net and off-net DDoS protection requirements.
Maximum Protection
Maximum Protection
Safeguard against large-scale attacks from any location while maintaining service continuity with our multi-terabit, globally extended network.
Cost-Effective Protection
Cost-Effective Protection
Leverage a transparent and predictable pricing model that is based on your internet bandwidth – only pay for what you use!
Unmatched Support
Unmatched Support
Attain peace of mind with unparalleled service level agreements, featuring our dedicated 24/7 DDoS response team, high-availability network performance and optimal mitigation times.
Seamless DDoS Defense
Seamless DDoS Defense
Reduce mitigation time and maintain low latency levels, even under attack, with inline DDoS protection that automatically filters and cleanses internet traffic before it reaches your internet ports.
Flexible Options
Flexible Options
Benefit from a collaborative approach that caters to your exact on-net and off-net DDoS protection requirements.
Maximum Protection
Maximum Protection
Safeguard against large-scale attacks from any location while maintaining service continuity with our multi-terabit, globally extended network.
Cost-Effective Protection
Cost-Effective Protection
Leverage a transparent and predictable pricing model that is based on your internet bandwidth – only pay for what you use!
Unmatched Support
Unmatched Support
Attain peace of mind with unparalleled service level agreements, featuring our dedicated 24/7 DDoS response team, high-availability network performance and optimal mitigation times.
WHY CHOOSE C8 SECURE?
RELATED BLOGS
DOWNLOAD DATA SHEET
For more information, please download our solutions data sheet
Please fill out the form to download the data sheet.
Let’s Get Started
Frequently Asked Questions
What is a DDoS attack?
A DDoS attack is like an unexpected traffic jam on an otherwise free-flowing highway. The attacks attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming it with a flood of Internet traffic.
DDoS attacks leverage multiple compromised computer systems as sources of attack traffic, including computers and Internet of Things (IoT) devices. They involve networks of Internet-connected devices infected with malware, controlled remotely by attackers and forming a botnet.
Are there different types of DDoS attacks?
DDoS attacks come in various forms. DDoS attacks can be categorized into three main types based on which part of the network connection they target: Volumetric Attacks, Protocol Attacks and Application Layer Attacks. Learn more here
How do I protect my business from DDoS attacks?
The main challenge in mitigating a DDoS attack is distinguishing between legitimate traffic and attack traffic. For example, a legitimate surge from a product release differs from an attack surge from known attackers.
These attacks are also multi-vector. This means they use multiple pathways to overwhelm targets, making it harder to distinguish between attack and normal traffic. A layered approach, such as combining DNS amplification (targeting layers 3/4) with an HTTP flood (layer 7), requires varied strategies for mitigation.
Due to these complexities, protecting a site from DDoS attacks requires a multi-layered approach. In the event of unforeseen circumstances, having a clear plan in place for responding to DDoS attacks can minimize downtime and damage.
Learn more here







